Can you recall a time when you set up the strongest password you could think of on your device, but still got hacked?
We once believed that a strong password was enough to protect against cyber attacks and data breaches, but even unique passwords can now be breached by brute-force attacks.
In this guide, we will discuss passkeys, a better way of securing your information online, how to set it up, and how to use it.
What are passkeys?
A passkey is a form of digital authentication that is designed to be more secure and user friendly than traditional passwords.
It is a secure alternative that relies on your device’s fingerprint scanner, face recognition, PIN or uses cryptographic keys to verify your identity on websites or apps.
When you want to use your desktop or mobile device, the passkey is just like a secret code or token that’s going to prove who you are. It makes sure only you get in.
What are passwords?
A password is a unique set of characters, typically alphanumeric, that you use to verify your identity and grant access to devices or online accounts such as social media, email or banking apps.
Strong and unique passwords are secret words or phrases, one of the main ways to prove you are who you say you are when you’re using computers, websites, or other services. They help ensure only authorized users can access their accounts or information.
Are passkeys more secure than passwords?
Generally, people widely use passwords and can protect them with a password manager, strong and unique passwords, or by enabling two-factor authentication.
On the other hand, people use passkeys in multi-factor authentication (MFA) systems. These systems combine things you know, things you have, and things you are (like biometrics) with cryptographic keys to provide stronger security.”
They are a more reliable option for protecting digital access because of their resistance to common attack methods and strong authentication factors.
What are the differences between passkeys and passwords?
People often use the terms interchangeably, but there are some key differences between passkeys and passwords.
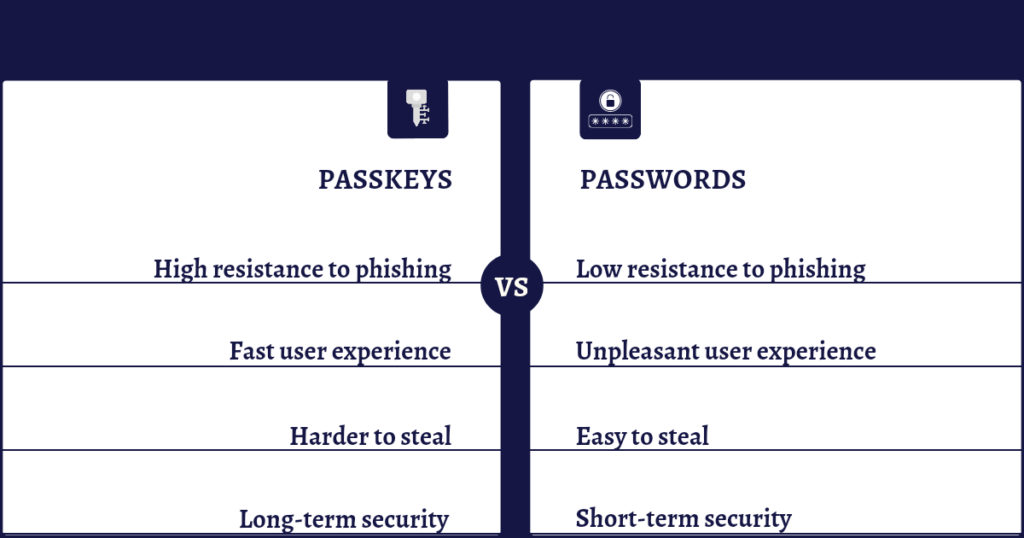
Passkeys are highly resistant to phishing unlike passwords.
Passwords are highly susceptible to phishing attacks. In these phishing attacks, attackers can trick you into entering your passwords and sensitive information on fake websites designed to look like legitimate ones.
They can then use this information to access your account, compromising your security.
In contrast, passkeys provide high resistance to phishing by utilizing local device verification methods, such as biometrics, or cryptographic keys.
These methods ensure that you do not disclose information to the websites or apps, making it extremely difficult for hackers to intercept or misuse the passkey. This makes it a secure option for verification.
Passkeys offer a smoother user experience than passwords.
Biometric passkeys, such as fingerprints or face recognition, are capable of instant access providing a faster and more comfortable experience.
Cryptographic keys often require simple actions like touching a security key, which makes it quick and easy to authenticate.
In contrast, users must remember and type complicated character sequences when they are using passwords. It can be tedious, prone to error, and burdensome, especially if you use different passwords for different accounts.
An unpleasant user experience can result from the process of managing passwords.
Passkeys are harder to steal than passwords.
Biometric data used for passkeys is unique to each user and is stored locally on your device, which makes it difficult for attackers to gain access. Additionally, secure protocols use cryptographic keys that are hard for attackers to intercept or replicate.
In contrast, attackers can steal passwords through various methods, such as brute-force attacks and data breaches. Using the same password across different sites can lead to one breach compromising multiple accounts, which increases the risk of passwords being stolen.
Passkeys provide better long-term security than passwords.
Passkeys are stronger against new attack techniques offering security on a long-term basis. Also, protocols are updated to maintain security without needing any action from the user, ensuring continuous protection against new threats.
In contrast, passwords can become less effective at protecting accounts as technology improves, allowing hackers to guess passwords more easily. They need to be changed regularly to remain secure, which can be inconvenient and challenging for users to manage.
3 steps to set up and use passkeys
Setting Up Passkeys:
- Ensure your mobile device or desktop supports passkeys.
- Enable your fingerprint or facial recognition in device settings.
Register Passkeys:
- Go to the security settings of the website or app you want to secure.
- Find the option to add passkeys and follow the instructions to set it up with your biometric data or a security key.
Using Passkeys:
- Use your fingerprint, face scan, or security key you used to register to log in.
- If you change devices, re-register your passkeys if needed.
- Regularly check your security settings to ensure your passkeys are up-to-date.
Final Thoughts
With passkeys, the future of a secure digital authentication that reduces cyber threats is at hand. While not yet available on all websites and apps, you can take proactive steps by checking if the passkey option is available on your devices and services today to enhance security of your online accounts. The use of passkeys, provides a more convenient and faster user experience when securing and verifying your information online.












